Microsoft Security Bulletin MS08-054 – Critical
Vulnerability in Windows Media Player Could Allow Remote Code Execution (954154)
Executive Summary
This security update resolves a privately reported vulnerability in Windows Media Player that could allow remote code execution when a specially crafted audio file is streamed from a Windows Media server. If a user is logged on with administrative user rights, an attacker who successfully exploited this vulnerability could take complete control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
This security update is rated Critical for all supported and affected editions of Windows Media Player 11. For more information, see the subsection, Affected and Non-Affected Software, in this section.
The security update addresses the vulnerability by correcting the manner in which Windows Media Player 11 handles audio files streamed from a server-side playlist (SSPL). For more information about the vulnerability, see the Frequently Asked Questions (FAQ) subsection for the specific vulnerability entry under the next section, Vulnerability Information.
Recommendation. Microsoft recommends that customers apply the update immediately.
24.10.08
20.10.08
Introducing Biometric Technology

Face Identification Technology
Facial biometrics is one of the fastest growing areas of biometrics. With growing technologies facial recognition can convert a photograph or a video image into a code that describes a face’s physical characterizes. This can be used to identify the common person from a distance, without intruding into their personal space.
Computer software for facial identification reads the peaks and valleys of an individual’s facial features; these peaks and valleys are known as nodal points. There are 80 nodal points in a human face, but the software needs only 15-20 to make an identification. Specialists concentrate on the golden triangle region between the temples and the lips. This area of the face remains the same even if hair and a beard is grown, weight is gained, aging occurs, or glasses are put on.

Hand Geometry Identification Technology
Hand geometry is a biometric that identifies users by the shape of their hands. Hand geometry readers measure a user's hand along many dimensions and compare those measurements to measurements stored in a file.
Viable hand geometry devices have been manufactured since the early 1980s, making hand geometry the first biometric to find widespread computerized use. It remains popular; common applications include access control and time-and-attendance operations.
Since hand geometry is not thought to be as unique as fingerprints or irises, fingerprinting and iris recognition remain the preferred technology for high-security applications. Hand geometry is very reliable when combined with other forms of identification, such as identification cards or personal identification numbers. In large populations, hand geometry is not suitable for so-called one-to-many applications, in which a user is identified from his biometric without any other identification.
Viable hand geometry devices have been manufactured since the early 1980s, making hand geometry the first biometric to find widespread computerized use. It remains popular; common applications include access control and time-and-attendance operations.
Since hand geometry is not thought to be as unique as fingerprints or irises, fingerprinting and iris recognition remain the preferred technology for high-security applications. Hand geometry is very reliable when combined with other forms of identification, such as identification cards or personal identification numbers. In large populations, hand geometry is not suitable for so-called one-to-many applications, in which a user is identified from his biometric without any other identification.

DNA Identification Technology
Deoxyribonucleic acid (DNA) Biometrics could be the most exact form of identifying any given individual (Baird, S., 2002). Every human being has its own individual map for every cell made, and this map, or ‘blueprint’ as it more often is called, can be found in every body cell. Because DNA is the structure that defines who we are physically and intellectually, unless an individual is an identical twin, it is not likely that any other person will have the same exact set of genes (Philipkoski, K., 2004).
DNA can be collected from any number of sources: blood, hair, finger nails, mouth swabs, blood stains, saliva, straws, and any number of other sources that has been attached to the body at some time. DNA matching has become a popular use in criminal trials, especially in proving rape cases (Landers, E., 1992). The main problems surrounding DNA biometrics is that it is not a quick process to identify someone by their DNA. The process is also a very costly one (Baird, S., 2002).
DNA Biometrics is not a fool proof method of identification. If forensic scientists to not conduct a DNA test properly, a person’s identification code can be skewed. Another problem is matching prior DNA samples to new samples; this is a bigger problem in DNA fingerprinting. The information looks like a bar code, and if not closely inspected an incorrect match could be made (SAIC, 2004).
DNA can be collected from any number of sources: blood, hair, finger nails, mouth swabs, blood stains, saliva, straws, and any number of other sources that has been attached to the body at some time. DNA matching has become a popular use in criminal trials, especially in proving rape cases (Landers, E., 1992). The main problems surrounding DNA biometrics is that it is not a quick process to identify someone by their DNA. The process is also a very costly one (Baird, S., 2002).
DNA Biometrics is not a fool proof method of identification. If forensic scientists to not conduct a DNA test properly, a person’s identification code can be skewed. Another problem is matching prior DNA samples to new samples; this is a bigger problem in DNA fingerprinting. The information looks like a bar code, and if not closely inspected an incorrect match could be made (SAIC, 2004).

Human Gait Identification Technology
Gait biometrics identifies a person by the way the walk, run, or any other type of motion of the legs. A person’s gait is the way in which they move on their feet. Gait biometrics can be used to identify everything from the length and thickness of an individuals legs to the stride of their step. Unlike some other, more researched and identifiable methods of biometrics, gait biometric technology faces the difficulty of identifying not only a particular body part but a motion (World Information, 2003).
At Georgia Tech University, professors and students are developing a system that will be able to recognize a persons gait by radar signals. This Doppler effect is 80- 95 percent effective in identifying an individual. Research Engineer Bill Marshall explains that they can decode radio signals reflecting of a person’s walking stride, as they walk toward the signal. This signal pattern is converted to an individuals audio signature, which can be catalogued for later use. Marshall is sure to include that audio signals, decoded from an individual’s gait, are not unique to a particular person. Any given number of people may have the same audio signature, but unlike the unique DNA or finger prints, gait biometrics can catalog an individual without them knowing they were ever being observed.
Gait biometrics would be particularly beneficial in identifying criminal suspects. Police could scan a large crowd for a suspect without them knowing they were on to them. Gait biometrics can also be used to identify shoplifters-particularly ‘pregnant’ women. Women pretending to be pregnant will walk differently then women who are actually pregnant. This would be a large advance in technology if introduced to common retail stores.
Some sources recognize what gait biometrics says it can do, but doubts it’s ability to perform. A gait system can easily be deceived because walking patterns can be sometimes be altered. Skeptics also doubt gait biometrics ability to perform in real life scenarios, such as airports and large crowds. Regardless of what critics say, gait biometrics will have to prove it’s capabilities in action.
At Georgia Tech University, professors and students are developing a system that will be able to recognize a persons gait by radar signals. This Doppler effect is 80- 95 percent effective in identifying an individual. Research Engineer Bill Marshall explains that they can decode radio signals reflecting of a person’s walking stride, as they walk toward the signal. This signal pattern is converted to an individuals audio signature, which can be catalogued for later use. Marshall is sure to include that audio signals, decoded from an individual’s gait, are not unique to a particular person. Any given number of people may have the same audio signature, but unlike the unique DNA or finger prints, gait biometrics can catalog an individual without them knowing they were ever being observed.
Gait biometrics would be particularly beneficial in identifying criminal suspects. Police could scan a large crowd for a suspect without them knowing they were on to them. Gait biometrics can also be used to identify shoplifters-particularly ‘pregnant’ women. Women pretending to be pregnant will walk differently then women who are actually pregnant. This would be a large advance in technology if introduced to common retail stores.
Some sources recognize what gait biometrics says it can do, but doubts it’s ability to perform. A gait system can easily be deceived because walking patterns can be sometimes be altered. Skeptics also doubt gait biometrics ability to perform in real life scenarios, such as airports and large crowds. Regardless of what critics say, gait biometrics will have to prove it’s capabilities in action.

Most wanted top 10 security analyzer
VisualRoute 2008 12.0h (updated 7 August 2008)VisualRoute delivers the functionality of key Internet "ping," "whois," and "traceroute" tools, in a high-speed visually integrated package.
Proxy / ISA Log Analyzer 2.61 (updated 28 May 2008)Proxy/ISA Log Analyzer is a high performance log analyzer that allows you to analyze and quickly generate useful reports on Internet connection usage based on data from logs created by Microsoft Proxy Server 2.0 or Microsoft ISA Server log files.
Security System Analyzer 1.6b2 (updated 21 April 2008)Security System Analyzer is free non-intrusive OVAL-Compatible software. It provides security testers, auditors with an advanced overview of the security policy level applied.
eMailTrackerPro 7.0i (updated 18 January 2008)Identify the sender of email messages, trace and report spammers, identify ‘phishing’ emails and other scammers trying to steal your confidential information.
GFI WebMonitor for ISA Server 4 (updated 22 October 2007)GFI WebMonitor for Microsoft ISA Server allows you to monitor HTTP and FTP downloads for viruses and other malware – in REAL TIME.
GFI EventsManager 7 (updated 3 February 2007)This program monitors the security event logs of all your Windows NT/2000/XP servers and workstations and alerts you to possible intrusions/attacks in real time.
WFP Tools 1.0 (updated 18 January 2006)WFP Tools allows the replacement of the infected/corrupted file with the original clean file you had when Windows was first installed thus avoiding reformatting your computer.
ZoneLog Analyser 1.19 (updated 2 February 2004)ZoneLog Analyser reads and displays the log file generated by ZoneLabs' ZoneAlarm.
proDETECT 0.2b (updated 24 March 2003)proDETECT is an open source promiscious mode scanner with a GUI.
VisualZone 5.7 (updated 10 September 2002)VisualZone is an intrusion analyser and report utility for ZoneAlarm, ZoneAlarm Plus and ZoneAlarm Pro.
Proxy / ISA Log Analyzer 2.61 (updated 28 May 2008)Proxy/ISA Log Analyzer is a high performance log analyzer that allows you to analyze and quickly generate useful reports on Internet connection usage based on data from logs created by Microsoft Proxy Server 2.0 or Microsoft ISA Server log files.
Security System Analyzer 1.6b2 (updated 21 April 2008)Security System Analyzer is free non-intrusive OVAL-Compatible software. It provides security testers, auditors with an advanced overview of the security policy level applied.
eMailTrackerPro 7.0i (updated 18 January 2008)Identify the sender of email messages, trace and report spammers, identify ‘phishing’ emails and other scammers trying to steal your confidential information.
GFI WebMonitor for ISA Server 4 (updated 22 October 2007)GFI WebMonitor for Microsoft ISA Server allows you to monitor HTTP and FTP downloads for viruses and other malware – in REAL TIME.
GFI EventsManager 7 (updated 3 February 2007)This program monitors the security event logs of all your Windows NT/2000/XP servers and workstations and alerts you to possible intrusions/attacks in real time.
WFP Tools 1.0 (updated 18 January 2006)WFP Tools allows the replacement of the infected/corrupted file with the original clean file you had when Windows was first installed thus avoiding reformatting your computer.
ZoneLog Analyser 1.19 (updated 2 February 2004)ZoneLog Analyser reads and displays the log file generated by ZoneLabs' ZoneAlarm.
proDETECT 0.2b (updated 24 March 2003)proDETECT is an open source promiscious mode scanner with a GUI.
VisualZone 5.7 (updated 10 September 2002)VisualZone is an intrusion analyser and report utility for ZoneAlarm, ZoneAlarm Plus and ZoneAlarm Pro.
19.10.08
How to reset microsoft windows password
some guys ask me several times for windows password reset ! most of the time its useful
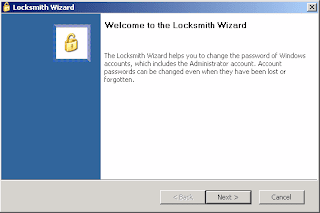
ERD Commander is part of the Microsoft Diagnostics and Recovery Toolset (DaRT) whose 30 day evaluation is available here (MSDaRT50Eval.msi - 64.2
MB). We’ve covered MS DaRT earlier in article Perform a System Restore rollback on a non-bootable Windows XP computer. Follow steps 1-7 in that article to create a ERD Commander Boot CD.
1. Insert the ERD Commander Boot CD into the drive and restart the system
2. Boot the computer using ERD Commander Boot CD. You may have to set the boot order in the BIOS first.
3. Select your Windows XP installation from the list
4. From the ERD Commander menu (Start menu), click System Tools and click Locksmith

5. reset whatever user u like
Break news

-->>South korean Army Under attack
The country's defense industry faces a serious security risk from hackers. Grand National Party lawmaker said Sunday based on data provided by the National Security Research Institute that LIGNex1, a guided missile manufacturer, uncovered malicious codes in its major computer systems planted by hackers in March, and Hyundai Heavy Industries, which makes naval vessels, found them in September.
LIGNex1 develops and manufactures Hyunmoo surface-to-surface missile, Haeseong ship-to-ship missile and Shingung portable ground-to-air weapons. Hyundai Heavy Industries manufactures Haeseong, the nation's first Aegis ship, plus destroyers and submarines for the Navy. Although the development costs of such high-tech weapons are kept secret, the construction of the King Sejong the Great-class destroyer is said to cost over W1 trillion (US$1=W1,165) and development of Haeseong ship-to-ship missile W100 billion with each missile at approximately W2 billion.
Source : Chosun Ilbo News paper , NSRI
-->>Teenage hacker charged for DDOS attack on Scientology
A teenager who took part in a distributed denial of service attack against the so-called church of Scientology has been charged.
Dmitriy Guzner, 18, of Verona, New Jersey, is charged with helping in the attack on Scientologist server in January. He has agreed to plead guilty to a single felony charge of unauthorized impairment of a protected computer and pay $37,500 in damages.
Guzner identifies himself as a member of the online group called ‘Anonymous’. The group is a loose collection of internet activist who undertake online activities, such as the attack on Scientology (dubbed Project Chanology), the tracking and arrest of suspected paedophile Chris Forcand and the hacking of vice-presidential candidate Sarah Palin’s email. The Justice Department has said that Guzner will be put on trial in the coming weeks and could face up to ten years in prison.
-->>Internet-scale 'man in the middle' attack disclosed
In Black Hat's October Webinar on Thursday, Anton Kapela, datacenter manager at 5Nines Data, spoke about Internet-scale "man in the middle" attacks.
The talk reprised a last-minute substitution presentation he gave along with Alexander Pilosov at this year's Defcon conference in August. During the conference, the two researchers intercepted all conference Internet traffic at the Riviera Hotel in Las Vegas and ran it through their servers. According to Black Hat founder and director Jeff Moss, most attendees didn't realizing this was being done.
"This is an emergent vulnerability," said Kapela in the Webinar. "It only becomes apparent in thousands of networks, not one." He took effort to explain that this is really a condition of the Internet today. "I'm not talking about any particular failing, or vendor implementation. This is something that happens because we're using it all," he said.
8.10.08
Break News
Hotmail and Gmail are under attack !!!!
CAPTCHA is a technique test of mail server that shown the user is human or software or machine , for protecting mail server against of dictionary attack and brute force!
THE REGISTER informs that spammers could be able to access these CAPTCHA and with this method they solve the first part of their attack. In the another report of securitylabs.websense.com another security company informed that Black hats hacked Hotmail CAPTCHA . It seems to be serious problem , take care about spams very much "Do not Open messeges with doubtful topics like VIAGRA ,SEX ,etc" .
Archive :
UK banks lost more than 300 billion pound in first half of 2008!
THE REGISTER informs most of these hackers use fake plastic card and stolen pin in some machine that they dont check card , these machines check pin and magnetic on the card ! with these methods Black hats gain more than 120 billion pounds . THE REGISTER infroms these event based on APACS ( the UK payment association ) .
They also reports that hackers use Phishing or Spy software to earn more and more . They are anxious about 20000 fake website ( PHISHING ) in the UK or outside .SANDRA QUEEN ( IT management of APACS ) told that they 've found a method for training users called "Be Card Smart Online " to be more safe and secure !
Source : APACS & THE REGISTER
6.10.08
Break news

Cracking one billion passwords per second with NVIDIA video cards
The new release of Elcomsoft Distributed Password Recovery reaches the recovery speed of one billion passwords per second by employing several NVIDIA video accelerators. Today's video cards such as NVIDIA GeForce GTX280 can process hundreds of billions fixed-point calculations per second. Add as much as 1 GB of onboard video memory and up to 240 processing units, multiply it by two by using a couple of NVIDIA cards, and enter the whole new world of super-parallel computational power for just a few hundred dollars. Unlike NVIDIA SLI mode, ElcomSoft has figured out how to unleash the computational power of several NVIDIA cards no matter whether or not they are of the same kind.Until recently, the abundance of highly parallel, super-scalar processors in 3D graphic accelerators could only be used for gaming. Today, ElcomSoft has found a way to reach into the future. The company has figured out how to put computational power provided by several NVIDIA boards working together to crack many kinds of passwords.
Until recently, the abundance of highly parallel, super-scalar processors in 3D graphic accelerators could only be used for gaming. Today, ElcomSoft has found a way to reach into the future. The company has figured out how to put computational power provided by several NVIDIA boards working together to crack many kinds of passwords.In February 2007, NVIDIA launched CUDA, a developer's kit that gives software developers access to the parallel processing power of the GPU. Modern NVIDIA GPUs act as powerful, highly parallel multiprocessors, with huge shared memory and cache.Elcomsoft Distributed Password Recovery can recover a variety of system passwords such as NTLM and startup passwords, crack MD5 hashes, unlock password-protected documents created by Microsoft Office 97-2007, PDF files created by Adobe Acrobat, as well as PGP and UNIX and Oracle user passwords. With the newest GPU acceleration upgrade of Elcomsoft Distributed Password Recovery the passwords will be recovered up to 25 times faster than by using CPU-only mode.
4.10.08
Zero day attacks

Definition : A zero-day exploit is one that takes advantage of a security vulnerability on the same day that the vulnerability becomes generally known. Ordinarily, after someone detects that a software program contains a potential exposure to exploitation by a hacker, that person or company can notify the software company and sometimes the world at large so that action can be taken to repair the exposure or defend against its exploitation. Given time, the software company can repair and distribute a fix to users. Even if potential hackers also learn of the vulnerability, it may take them some time to exploit it; meanwhile, the fix can hopefully become available first.
With experience, however, hackers are becoming faster at exploiting a vulnerability and sometimes a hacker may be the first to discover the vulnerability. In these situations, the vulnerability and the exploit may become apparent on the same day. Since the vulnerability isn't known in advance, there is no way to guard against the exploit before it happens. Companies exposed to such exploits can, however, institute procedures for early detection of an exploit.
A study released by Symantec in early 2004 found that although the number of vulnerabilities discovered was about the same in 2003 as in 2002, the time between the vulnerability and exploits based on it had narrowed. According to the infoAnarchy wiki, "14-day" groups and "7-day" groups carry out an exploit within 14 or 7 days of a product's market release. Conducting a zero-day exploit establishes crackers as members of the elite, because they must have covert industry connections to gain the inside information needed to carry out the attack.
With experience, however, hackers are becoming faster at exploiting a vulnerability and sometimes a hacker may be the first to discover the vulnerability. In these situations, the vulnerability and the exploit may become apparent on the same day. Since the vulnerability isn't known in advance, there is no way to guard against the exploit before it happens. Companies exposed to such exploits can, however, institute procedures for early detection of an exploit.
A study released by Symantec in early 2004 found that although the number of vulnerabilities discovered was about the same in 2003 as in 2002, the time between the vulnerability and exploits based on it had narrowed. According to the infoAnarchy wiki, "14-day" groups and "7-day" groups carry out an exploit within 14 or 7 days of a product's market release. Conducting a zero-day exploit establishes crackers as members of the elite, because they must have covert industry connections to gain the inside information needed to carry out the attack.
Archive : Kasper Kicked .

The official Malaysian Kaspersky Antivirus's website has been hacked yesterday by a Turkish cracker going by the handle of "m0sted". Along with it, the same cracker hacked also the official Kaspersky S.E.S. online shop and its several other subdomains. The attacker reported "patriotism" as the reason behind the attack and "SQL Injection" as the technical way the intrusion was performed. Both websites has been home page defaced as well as several other secondary pages. The incident, though appearing a simple website defacement, might carry along big risks for end-users because from both the websites, evaluation copies of the Kaspersky Antivirus are distributed to the public. In theory, the attacker could have uploaded trojanized versions of the antivirus, infecting in this way the unaware users attempting a download from a trusted Kaspersky's file repository (remember the trojan in the Debian file repository?).
Subscribe to:
Posts (Atom)





